Not all Virtual Private Networks (VPNs) are created equal.
There are so many flavors of VPNs to boggle the imagination.
Purists insist that, strictly speaking, a VPN is not even required to have encryption. Of course, the same purists would concede that IPsec is a must have add-on for a VPN to truly fulfill its purpose of providing a secure tunnel.
In the corporate world, whether it’s a site-to-site VPN or a more complex DMVPN a secure VPN is a sine qua non.
In the VPN universe, IKEv1 is slowly making way to the more secure IKEv2.
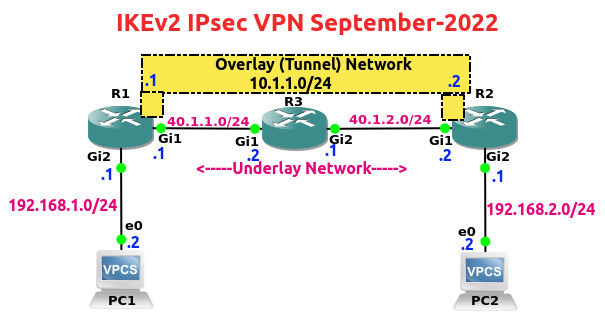
In this post, we’ll configure a site-to-site IKEv2 VPN and run a bunch of show commands.
This post is not meant for someone completely new to networking. I’m assuming readers will have at least CCNA-level knowledge of IP addressing, subnets, routing, network security and VPNs.
IKEv2 Configuration
The IP addresses of the three routers and end-devices have already been configured.
I’ve highlighted the overlay and underlay interfaces, IP addresses and networks in the topology above.
IKEv2 VPN Configuration – 8 Steps
For convenience and easy understanding, I’ve divided the configuration of our Site-to-Site IKEv2 VPN into eight steps:
1. IKEv2 Proposal
2. IKEv2 Policy
3. IKEv2 Keyring
4. IKEv2 Profile
5. IPsec Transformset
6. IPsec Profile
7. Tunnel Interface
8. Routing
=========================
R1 Configuration
Step 1. IKEv2 Proposal
conf t
crypto ikev2 proposal December-Proposal
encryption aes-cbc-256
integrity sha512
group 21
exit
Step 2. IKEv2 Policy
crypto ikev2 policy November-Policy
match address local 40.1.1.1
proposal December-Proposal
exit
Step 3. IKEv2 Keyring
crypto ikev2 keyring October-KEYRING
peer R2
address 40.1.2.2
pre-shared-key local R1key
pre-shared-key remote R2key
exit
exit
Step 4. IKEv2 Profile
crypto ikev2 profile September-PROFILE
authentication local pre-share
authentication remote pre-share
keyring local October-KEYRING
match identity remote address 40.1.2.2
identity local address 40.1.1.1
exit
Step 5. IPsec Transformset
crypto ipsec transform-set BT-SET esp-aes 256 esp-sha256-hmac
exit
Step 6. IPsec Profile
crypto ipsec profile BOB-IPSEC-PROFILE
set transform-set BT-SET
set ikev2-profile September-PROFILE
exit
Step 7. Configure Tunnel Interface
int tunnel 0
ip address 10.1.1.1 255.255.255.0
tunnel source 40.1.1.1
tunnel destination 40.1.2.2
tunnel mode ipsec ipv4
tunnel protection ipsec profile BOB-IPSEC-PROFILE
no shut
exit
Step 8. Configure Routing
router eigrp 20
no auto-summary
network 192.168.1.0 0.0.0.255
network 10.1.1.0 0.0.0.255
exit
================
R2 Configuration
Step 1. IKEv2 Proposal
conf t
crypto ikev2 proposal December-Proposal
encryption aes-cbc-256
integrity sha512
group 21
exit
Step 2. IKEv2 Policy
crypto ikev2 policy November-Policy
match address local 40.1.2.2
proposal December-Proposal
exit
Step 3. IKEv2 Keyring
crypto ikev2 keyring October-KEYRING
peer R1
address 40.1.1.1
pre-shared-key local R2key
pre-shared-key remote R1key
exit
exit
Step 4. IKEv2 Profile
crypto ikev2 profile September-PROFILE
authentication local pre-share
authentication remote pre-share
keyring local October-KEYRING
match identity remote address 40.1.1.1
identity local address 40.1.2.2
exit
Step 5. IPsec Transformset
crypto ipsec transform-set BT-SET esp-aes 256 esp-sha256-hmac
exit
Step 6. IPsec Profile
crypto ipsec profile BOB-IPSEC-PROFILE
set transform-set BT-SET
set ikev2-profile September-PROFILE
exit
Step 7. Configure Tunnel Interface
int tunnel 0
ip address 10.1.1.2 255.255.255.0
tunnel source 40.1.2.2
tunnel destination 40.1.1.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile BOB-IPSEC-PROFILE
no shut
exit
Step 8. Configure Routing
router eigrp 20
no auto-summary
network 192.168.2.0 0.0.0.255
network 10.1.1.0 0.0.0.255
exit
==================
Some Useful IKEv2 Verify Commands
show crypto ipsec sa
show crypto session
show run | section Crypto
show crypto engine accelerator statistic
show int tunnel 0
show crypto ikev2 proposal
show crypto ikev2 policy
debug crypto engine packet
debug crypto ikev2 packet
Verifing our Crypto Configuration on R1
R1#sh run | sec crypto
[output truncated]
crypto ikev2 proposal December-Proposal
encryption aes-cbc-256
integrity sha512
group 21
crypto ikev2 policy November-Policy
match address local 40.1.1.1
proposal December-Proposal
crypto ikev2 keyring October-KEYRING
peer R2
address 40.1.2.2
pre-shared-key local R1key
pre-shared-key remote R2key
!
crypto ikev2 profile September-PROFILE
match identity remote address 40.1.2.2 255.255.255.255
identity local address 40.1.1.1
authentication remote pre-share
authentication local pre-share
keyring local October-KEYRING
crypto ipsec transform-set BT-SET esp-aes 256 esp-sha256-hmac
mode tunnel
crypto ipsec profile BOB-IPSEC-PROFILE
set transform-set BT-SET
set ikev2-profile September-PROFILE
R1#
Verifing our Crypto Configuration on R2
R2#sh run | sec crypto
[output truncated]
crypto pki certificate chain TP-self-signed-3202180324
crypto ikev2 proposal December-Proposal
encryption aes-cbc-256
integrity sha512
group 21
crypto ikev2 policy November-Policy
match address local 40.1.2.2
proposal December-Proposal
crypto ikev2 keyring October-KEYRING
peer R1
address 40.1.1.1
pre-shared-key local R2key
pre-shared-key remote R1key
!
crypto ikev2 profile September-PROFILE
match identity remote address 40.1.1.1 255.255.255.255
identity local address 40.1.2.2
authentication remote pre-share
authentication local pre-share
keyring local October-KEYRING
crypto ipsec transform-set BT-SET esp-aes 256 esp-sha256-hmac
mode tunnel
crypto ipsec profile BOB-IPSEC-PROFILE
set transform-set BT-SET
set ikev2-profile September-PROFILE
R2#
Checking Interfaces on R1
R1#sh ip int brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet1 40.1.1.1 YES manual up up
GigabitEthernet2 192.168.1.1 YES manual up up
GigabitEthernet3 unassigned YES unset administratively down down
GigabitEthernet4 unassigned YES unset administratively down down
Tunnel0 10.1.1.1 YES manual up up
Verifying PC1 to PC2 Connectivity
Successful pings and trace routes on the two end-devices confirm that our tunnel0 is working fine.
PC1 is able to ping PC2 and vice versa.
PC1> ping 192.168.2.2
192.168.2.2 icmp_seq=1 timeout
84 bytes from 192.168.2.2 icmp_seq=2 ttl=62 time=7.263 ms
84 bytes from 192.168.2.2 icmp_seq=3 ttl=62 time=6.157 ms
84 bytes from 192.168.2.2 icmp_seq=4 ttl=62 time=5.959 ms
84 bytes from 192.168.2.2 icmp_seq=5 ttl=62 time=8.569 ms
PC1> trace 192.168.2.2
trace to 192.168.2.2, 8 hops max, press Ctrl+C to stop
1 192.168.1.1 5.999 ms 2.019 ms 1.617 ms
2 10.1.1.2 12.953 ms 3.600 ms 4.169 ms
3 *192.168.2.2 9.599 ms (ICMP type:3, code:3, Destination port unreachable)
PC1>
PC2> ping 192.168.1.1
84 bytes from 192.168.1.1 icmp_seq=1 ttl=254 time=13.269 ms
84 bytes from 192.168.1.1 icmp_seq=2 ttl=254 time=4.614 ms
84 bytes from 192.168.1.1 icmp_seq=3 ttl=254 time=5.469 ms
84 bytes from 192.168.1.1 icmp_seq=4 ttl=254 time=5.382 ms
84 bytes from 192.168.1.1 icmp_seq=5 ttl=254 time=4.964 ms
PC2> trace 192.168.1.1
trace to 192.168.1.1, 8 hops max, press Ctrl+C to stop
1 192.168.2.1 3.267 ms 7.103 ms 2.253 ms
2 *10.1.1.1 28.731 ms (ICMP type:3, code:3, Destination port unreachable) *
PC2>
===============================================
Verifying Routing on R1
The show ip route command shows that the 192.168.2.0 is being reached via the overlay network (see below).
R1#sh ip route
Codes: L – local, C – connected, S – static, R – RIP, M – mobile, B – BGP
D – EIGRP, EX – EIGRP external, O – OSPF, IA – OSPF inter area
N1 – OSPF NSSA external type 1, N2 – OSPF NSSA external type 2
E1 – OSPF external type 1, E2 – OSPF external type 2
i – IS-IS, su – IS-IS summary, L1 – IS-IS level-1, L2 – IS-IS level-2
ia – IS-IS inter area, * – candidate default, U – per-user static route
o – ODR, P – periodic downloaded static route, H – NHRP, l – LISP
a – application route
+ – replicated route, % – next hop override, p – overrides from PfR
Gateway of last resort is 40.1.1.2 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 40.1.1.2
10.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 10.1.1.0/24 is directly connected, Tunnel0
L 10.1.1.1/32 is directly connected, Tunnel0
40.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 40.1.1.0/24 is directly connected, GigabitEthernet1
L 40.1.1.1/32 is directly connected, GigabitEthernet1
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, GigabitEthernet2
L 192.168.1.1/32 is directly connected, GigabitEthernet2
D 192.168.2.0/24 [90/26880256] via 10.1.1.2, 00:37:51, Tunnel0
R1#sh ip route 192.168.2.2
Routing entry for 192.168.2.0/24
Known via “eigrp 20”, distance 90, metric 26880256, type internal
Redistributing via eigrp 20
Last update from 10.1.1.2 on Tunnel0, 00:38:18 ago
Routing Descriptor Blocks:
* 10.1.1.2, from 10.1.1.2, 00:38:18 ago, via Tunnel0
Route metric is 26880256, traffic share count is 1
Total delay is 50010 microseconds, minimum bandwidth is 100 Kbit
Reliability 255/255, minimum MTU 1438 bytes
Loading 1/255, Hops 1
R1#
================================
Some Crypto Verify Commands on R1
Now it’s time to get going with a bunch of crypto commands and examine the output.
R1#show crypto ikev2 sa detailed
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 40.1.1.1/500 40.1.2.2/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:21, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/3224 sec
CE id: 1001, Session-id: 1
Status Description: Negotiation done
Local spi: 0F77C00D167A34BE Remote spi: F14374F7D1885E3D
Local id: 40.1.1.1
Remote id: 40.1.2.2
Local req msg id: 0 Remote req msg id: 2
Local next msg id: 0 Remote next msg id: 2
Local req queued: 0 Remote req queued: 2
Local window: 5 Remote window: 5
DPD configured for 0 seconds, retry 0
Fragmentation not configured.
Dynamic Route Update: enabled
Extended Authentication not configured.
NAT-T is not detected
Cisco Trust Security SGT is disabled
Initiator of SA : No
IPv6 Crypto IKEv2 SA
R1#
================================
R1#show crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 40.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer 40.1.2.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 740, #pkts encrypt: 740, #pkts digest: 740
#pkts decaps: 740, #pkts decrypt: 740, #pkts verify: 740
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 40.1.1.1, remote crypto endpt.: 40.1.2.2
plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1
current outbound spi: 0xA5DADA1A(2782583322)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xA7E95D48(2817088840)
transform: esp-256-aes esp-sha256-hmac ,
in use settings ={Tunnel, }
conn id: 2004, flow_id: CSR:4, sibling_flags FFFFFFFF80000048, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4607999/3596)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xA5DADA1A(2782583322)
transform: esp-256-aes esp-sha256-hmac ,
in use settings ={Tunnel, }
conn id: 2003, flow_id: CSR:3, sibling_flags FFFFFFFF80000048, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4607999/3596)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
================================
R1#show crypto session
Crypto session current status
Interface: Tunnel0
Profile: September-PROFILE
Session status: UP-ACTIVE
Peer: 40.1.2.2 port 500
Session ID: 2
IKEv2 SA: local 40.1.1.1/500 remote 40.1.2.2/500 Active
IPSEC FLOW: permit ip 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0
Active SAs: 2, origin: crypto map
================================
Some Crypto Verify Commands on R2
R2#show crypto ikev2 sa detailed
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 40.1.2.2/500 40.1.1.1/500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA512, Hash: SHA512, DH Grp:21, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/246 sec
CE id: 1001, Session-id: 1
Status Description: Negotiation done
Local spi: F14374F7D1885E3D Remote spi: 0F77C00D167A34BE
Local id: 40.1.2.2
Remote id: 40.1.1.1
Local req msg id: 2 Remote req msg id: 0
Local next msg id: 2 Remote next msg id: 0
Local req queued: 2 Remote req queued: 0
Local window: 5 Remote window: 5
DPD configured for 0 seconds, retry 0
Fragmentation not configured.
Dynamic Route Update: enabled
Extended Authentication not configured.
NAT-T is not detected
Cisco Trust Security SGT is disabled
Initiator of SA : Yes
IPv6 Crypto IKEv2 SA
================================
R2#show crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 40.1.2.2
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer 40.1.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 86, #pkts encrypt: 86, #pkts digest: 86
#pkts decaps: 87, #pkts decrypt: 87, #pkts verify: 87
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 40.1.2.2, remote crypto endpt.: 40.1.1.1
plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet1
current outbound spi: 0x533E0924(1396574500)
PFS (Y/N): N, DH group: noneDecember-Proposal
inbound esp sas:
spi: 0x30612CC1(811674817)
transform: esp-256-aes esp-sha256-hmac ,
in use settings ={Tunnel, }
conn id: 2002, flow_id: CSR:2, sibling_flags FFFFFFFF80000048, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4607990/3244)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x533E0924(1396574500)
transform: esp-256-aes esp-sha256-hmac ,
in use settings ={Tunnel, }
conn id: 2001, flow_id: CSR:1, sibling_flags FFFFFFFF80000048, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4607994/3244)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
================================
R2#show crypto session
Crypto session current status
Interface: Tunnel0
Profile: September-PROFILE
Session status: UP-ACTIVE
Peer: 40.1.1.1 port 500
Session ID: 1
IKEv2 SA: local 40.1.2.2/500 remote 40.1.1.1/500 Active
IPSEC FLOW: permit ip 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0
Active SAs: 2, origin: crypto map
Overall, it seems like our IKEv2 Site-to-Site VPN configuration is working fine.

Sorry, the comment form is closed at this time.