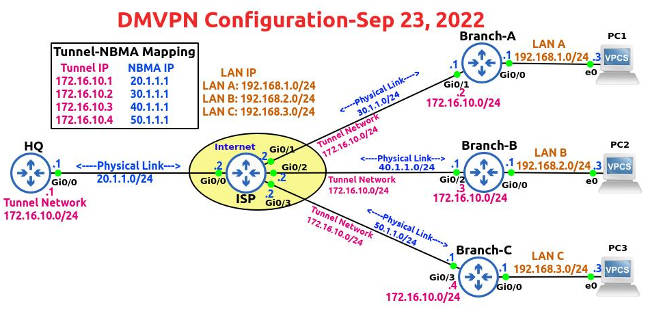
Dynamic Multipoint Virtual Private Network (DMVPN) owes its popularity to two primary reasons: scalability and simplicity of configuration.
In large organizations with lots of branches, configuring dozens of point-to-point VPN tunnels is an error-prone and cumbersome exercise.
So Cisco introduced the DMVPN technology nearly two decades ago.
DMVPN finds favor for another reason: It supports all routing protocols except IS-IS.
DMVPN Foundation Technologies
* Next Hop Resolution Protocol (NHRP): A layer 2 resolution protocol and cache used in DMVPN to map a tunnel IP address to an Non-Broadcast Multicast (NBMA) public IP address.
* Multipoint GRE (mGRE) interface: A single GRE interface that supports multiple GRE/IPsec tunnels and endpoints; also unlike with regular GRE, we do not define a tunnel destination with mGRE tunnels.
* IPsec: For protecting the DMVPN tunnels; both IKEv1 and IKEv2 are supported; DMVPN can be deployed without IPsec encryption but why would you want to.
Over the years, DMVPN has evolved through three phases but the current focus is only on Phase 3.
DMVPN – Phase 3 Configuration
In our topology (see at the top of this post), the IP addresses of the routers and PCs have already been configured.
You can check the IP address, Network ID, Subnet Mask and Interface IDs in the topology diagram.
So we’ll get straight down to DMVPN and IPsec configuration.
Toward the end of this post, we’ll run a few show commands.
! DMVPN Configuration
HQ is our Hub router and Branch A, Branch B and Branch C are the Spoke routers.
! HQ Router
! Configure Default Static Route on HQ Router
conf t
ip route 0.0.0.0 0.0.0.0 20.1.1.2
exit
!mGRE Configuration on HQ (Hub) Router
Configure Tunnel
conf t
interface tunnel 0
ip address 172.16.10.1 255.255.255.0
ip mtu 1400
ip tcp adjust-mss 1360
tunnel source gig0/0
tunnel mode gre multipoint
tunnel key 123
no shut
exit
! Configuring NHRP on Tunnel Interfaces of HQ Router
interface tunnel 0
ip nhrp network-id 1
ip nhrp authentication Cisco567
ip nhrp map multicast dynamic
ip nhrp redirect
exit
!Configure Dynamic Routing
router eigrp 5
network 172.16.10.0 0.0.0.255
no auto-summary
end
! Configure EIGRP Hop Issues on HQ (Hub) Router
conf t
interface tunnel 0
no ip next-hop-self eigrp 5
no ip split-horizon eigrp 5
exit
============================
Let’s configure the Spoke Routers (aka Branch Routers) now.
! Branch-A Router Configuration
Configure Default Static Route to ISP Router
conf t
ip route 0.0.0.0 0.0.0.0 30.1.1.2
end
!mGRE Configuration on Branch-A
Configure Tunnel on Branch A
conf t
interface tunnel 0
ip address 172.16.10.2 255.255.255.0
ip mtu 1400
ip tcp adjust-mss 1360
tunnel source g0/1
tunnel mode gre multipoint
tunnel key 123
no shut
! Configuring NHRP Inside the Tunnel Interfaces
conf t
interface tunnel 0
ip nhrp network-id 1
ip nhrp authentication Cisco567
ip nhrp map 172.16.10.1 20.1.1.1
ip nhrp map multicast 20.1.1.1
ip nhrp nhs 172.16.10.1
ip nhrp shortcut
exit
! Configure Dynamic Routing (Tunnel & LAN)
conf t
router eigrp 5
network 172.16.10.0 0.0.0.255
network 192.168.1.0 0.0.0.255
no auto-summary
end
============================
! Branch-B Router Configuration
Configure Default Static Route to ISP Router
conf t
ip route 0.0.0.0 0.0.0.0 40.1.1.2
end
!mGRE Configuration on Branch-B
Configure Tunnel
conf t
interface tunnel 0
ip address 172.16.10.3 255.255.255.0
ip mtu 1400
ip tcp adjust-mss 1360
tunnel source gig0/2
tunnel mode gre multipoint
tunnel key 123
no shut
exit
! Configuring NHRP on Tunnel Interfaces
interface tunnel 0
ip nhrp network-id 1
ip nhrp authentication Cisco567
ip nhrp map 172.16.10.1 20.1.1.1
ip nhrp map multicast 20.1.1.1
ip nhrp nhs 172.16.10.1
ip nhrp shortcut
exit
! Configure Dynamic Routing (Tunnel & LAN)
router eigrp 5
network 192.168.2.0 0.0.0.255
network 172.16.10.0 0.0.0.255
no auto-summary
end
============================
! Branch-C Router Configuration
Configure Default Static Route to ISP Router
conf t
ip route 0.0.0.0 0.0.0.0 50.1.1.2
!mGRE Configuration on Branch-C
Configure Tunnel
interface tunnel 0
ip address 172.16.10.4 255.255.255.0
ip mtu 1400
ip tcp adjust-mss 1360
tunnel source g0/3
tunnel mode gre multipoint
sh ip int br
tunnel key 123
no shut
exit
! Configuring NHRP on the Tunnel Interfaces
interface tunnel 0
ip nhrp network-id 1
ip nhrp authentication Cisco567
ip nhrp map 172.16.10.1 20.1.1.1
ip nhrp map multicast 20.1.1.1
ip nhrp nhs 172.16.10.1
ip nhrp shortcut
exit
! Configure Dynamic Routing (Tunnel & LAN)
router eigrp 5
network 192.168.3.0 0.0.0.255
network 172.16.10.0 0.0.0.255
no auto-summary
end
============================
IPsec Configuration
Let’s now work on the IPsec configuration on the Hub and Spokes.
Apply IPSec Configuration to Routers
HQ Router
conf t
crypto isakmp policy 25
hash sha256
authentication pre-share
group 16
encryption aes 256
exit
crypto isakmp key Cisco123! address 0.0.0.0 0.0.0.0
crypto ipsec transform-set JACK esp-aes 256 esp-sha256-hmac
exit
crypto ipsec profile JAN-2022
set transform-set JACK
interface tunnel 0
tunnel protection ipsec profile JAN-2022
Branch-A Router
conf t
crypto isakmp policy 25
hash sha256
authentication pre-share
encryption aes 256
group 16
exit
crypto isakmp key Cisco123! address 0.0.0.0 0.0.0.0
crypto ipsec transform-set JACK esp-aes 256 esp-sha256-hmac
exit
crypto ipsec profile JAN-2022
set transform-set JACK
exit
interface tunnel 0
tunnel protection ipsec profile JAN-2022
exit
===================================
Branch-B Router
conf t
crypto isakmp policy 25
hash sha256
authentication pre-share
encryption aes 256
group 16
exit
crypto isakmp key Cisco123! address 0.0.0.0 0.0.0.0
crypto ipsec transform-set JACK esp-aes 256 esp-sha256-hmac
exit
crypto ipsec profile JAN-2022
set transform-set JACK
exit
interface tunnel 0
tunnel protection ipsec profile JAN-2022
exit
===================================
Branch-C Router
conf t
crypto isakmp policy 25
hash sha256
authentication pre-share
encryption aes 256
group 16
exit
crypto isakmp key Cisco123! address 0.0.0.0 0.0.0.0
crypto ipsec transform-set JACK esp-aes 256 esp-sha256-hmac
exit
crypto ipsec profile JAN-2022
set transform-set JACK
exit
interface tunnel 0
tunnel protection ipsec profile JAN-2022
exit
===================================
Verify DMVPN/IPsec
Let’s run a bunch of show commands now.
Branch-A#show dmvpn
Legend: Attrb –> S – Static, D – Dynamic, I – Incomplete
N – NATed, L – Local, X – No Socket
T1 – Route Installed, T2 – Nexthop-override
C – CTS Capable
# Ent –> Number of NHRP entries with same NBMA peer
NHS Status: E –> Expecting Replies, R –> Responding, W –> Waiting
UpDn Time –> Up or Down Time for a Tunnel
==========================================================================
Interface: Tunnel0, IPv4 NHRP Details
Type:Spoke, NHRP Peers:1,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
—– ————— ————— —– ——– —–
1 20.1.1.1 172.16.10.1 UP 00:11:18 S
Two Trace Route Tests
In the first trace route test, we notice that PC1 goes via the Hub, i.e., HQ router but in the second Ping we see the direct Spoke-to-Spoke communication.
Trace Route Test 1
PC1> trace 192.168.3.3
trace to 192.168.3.3, 8 hops max, press Ctrl+C to stop
1 192.168.1.1 9.130 ms 4.943 ms 3.239 ms
2 172.16.10.1 28.634 ms 26.395 ms 24.367 ms
3 172.16.10.4 55.470 ms 56.578 ms 51.083 ms
4 *192.168.3.3 92.779 ms (ICMP type:3, code:3, Destination port unreachable)
Trace Route Test 2
PC1> trace 192.168.3.3
trace to 192.168.3.3, 8 hops max, press Ctrl+C to stop
1 192.168.1.1 5.135 ms 4.122 ms 4.057 ms
2 172.16.10.4 30.269 ms 22.106 ms 15.984 ms
3 *192.168.3.3 20.189 ms (ICMP type:3, code:3, Destination port unreachable)
Branch-A#show dmvpn
Legend: Attrb –> S – Static, D – Dynamic, I – Incomplete
N – NATed, L – Local, X – No Socket
T1 – Route Installed, T2 – Nexthop-override
C – CTS Capable
# Ent –> Number of NHRP entries with same NBMA peer
NHS Status: E –> Expecting Replies, R –> Responding, W –> Waiting
UpDn Time –> Up or Down Time for a Tunnel
==========================================================================
Interface: Tunnel0, IPv4 NHRP Details
Type:Spoke, NHRP Peers:2,
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb
—– ————— ————— —– ——– —–
1 20.1.1.1 172.16.10.1 UP 00:12:21 S
2 50.1.1.1 172.16.10.4 UP 00:00:22 DT1
172.16.10.4 UP 00:00:22 DT2
Branch-A#show ip nhrp shortcut
172.16.10.4/32 via 172.16.10.4
Tunnel0 created 00:03:59, expire 01:56:01
Type: dynamic, Flags: router nhop rib
NBMA address: 50.1.1.1
192.168.3.0/24 via 172.16.10.4
Tunnel0 created 00:03:58, expire 01:56:00
Type: dynamic, Flags: router rib nho
NBMA address: 50.1.1.1
Branch-A#
Branch-A#show dmvpn detail
Legend: Attrb –> S – Static, D – Dynamic, I – Incomplete
N – NATed, L – Local, X – No Socket
T1 – Route Installed, T2 – Nexthop-override
C – CTS Capable
# Ent –> Number of NHRP entries with same NBMA peer
NHS Status: E –> Expecting Replies, R –> Responding, W –> Waiting
UpDn Time –> Up or Down Time for a Tunnel
==========================================================================
Interface Tunnel0 is up/up, Addr. is 172.16.10.2, VRF “”
Tunnel Src./Dest. addr: 30.1.1.1/MGRE, Tunnel VRF “”
Protocol/Transport: “multi-GRE/IP”, Protect “JAN-2022”
Interface State Control: Disabled
nhrp event-publisher : Disabled
IPv4 NHS:
172.16.10.1 RE priority = 0 cluster = 0
Type:Spoke, Total NBMA Peers (v4/v6): 3
# Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb Target Network
—– ————— ————— —– ——– —– —————–
1 20.1.1.1 172.16.10.1 UP 00:20:03 S 172.16.10.1/32
2 50.1.1.1 172.16.10.4 UP 00:08:05 DT1 172.16.10.4/32
50.1.1.1 172.16.10.4 UP 00:08:05 DT2 192.168.3.0/24
1 30.1.1.1 172.16.10.2 UP 00:08:05 DLX 192.168.1.0/24
Crypto Session Details:
——————————————————————————–
Interface: Tunnel0
Session: [0x10D7B838]
Session ID: 0
IKEv1 SA: local 30.1.1.1/500 remote 20.1.1.1/500 Active
Capabilities:(none) connid:1001 lifetime:23:39:54
Crypto Session Status: UP-ACTIVE
fvrf: (none), Phase1_id: 20.1.1.1
IPSEC FLOW: permit 47 host 30.1.1.1 host 20.1.1.1
Active SAs: 4, origin: crypto map
Inbound: #pkts dec’ed 279 drop 0 life (KB/Sec) 4286401/2395
Outbound: #pkts enc’ed 280 drop 0 life (KB/Sec) 4286401/2395
Outbound SPI : 0x46732BB6, transform : esp-256-aes esp-sha256-hmac
Socket State: Open
Interface: Tunnel0
Session: [0x10D7B930]
Session ID: 0
IKEv1 SA: local 30.1.1.1/500 remote 50.1.1.1/500 Active
Capabilities:(none) connid:1002 lifetime:23:51:54
Session ID: 0
IKEv1 SA: local 30.1.1.1/500 remote 50.1.1.1/500 Active
Capabilities:(none) connid:1003 lifetime:23:51:54
Crypto Session Status: UP-ACTIVE
fvrf: (none), Phase1_id: 50.1.1.1
IPSEC FLOW: permit 47 host 30.1.1.1 host 50.1.1.1
Active SAs: 4, origin: crypto map
Inbound: #pkts dec’ed 9 drop 0 life (KB/Sec) 4260667/3114
Outbound: #pkts enc’ed 8 drop 0 life (KB/Sec) 4260667/3114
Outbound SPI : 0x2DE78CC7, transform : esp-256-aes esp-sha256-hmac
Socket State: Open
Pending DMVPN Sessions:
Branch-A#
Ping Tests
Let’s run a couple of pings to verify reachability.
PC1> ping 192.168.3.3
84 bytes from 192.168.3.3 icmp_seq=1 ttl=62 time=33.569 ms
84 bytes from 192.168.3.3 icmp_seq=2 ttl=62 time=20.158 ms
84 bytes from 192.168.3.3 icmp_seq=3 ttl=62 time=25.318 ms
84 bytes from 192.168.3.3 icmp_seq=4 ttl=62 time=21.351 ms
84 bytes from 192.168.3.3 icmp_seq=5 ttl=62 time=23.523 ms
PC1> ping 192.168.2.3
84 bytes from 192.168.2.3 icmp_seq=1 ttl=61 time=75.934 ms
84 bytes from 192.168.2.3 icmp_seq=2 ttl=62 time=23.839 ms
84 bytes from 192.168.2.3 icmp_seq=3 ttl=62 time=21.544 ms
84 bytes from 192.168.2.3 icmp_seq=4 ttl=62 time=21.184 ms
84 bytes from 192.168.2.3 icmp_seq=5 ttl=62 time=21.815 ms
Branch-A#sh ip route next-hop-override | section H|%
o – ODR, P – periodic downloaded static route, H – NHRP, l – LISP
+ – replicated route, % – next hop override, p – overrides from PfR
H 172.16.10.3/32 is directly connected, 00:00:47, Tunnel0
H 172.16.10.4/32 is directly connected, 00:27:45, Tunnel0
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
D % 192.168.2.0/24 [90/28160256] via 172.16.10.3, 00:39:43, Tunnel0
[NHO][90/255] via 172.16.10.3, 00:00:47, Tunnel0
D % 192.168.3.0/24 [90/28160256] via 172.16.10.4, 00:39:43, Tunnel0
[NHO][90/255] via 172.16.10.4, 00:27:45, Tunnel0
Branch-A#
Verify Routing on Branch A & HQ Routers
Check Branch A Routing
Branch-A#show ip route
Codes: L – local, C – connected, S – static, R – RIP, M – mobile, B – BGP
D – EIGRP, EX – EIGRP external, O – OSPF, IA – OSPF inter area
N1 – OSPF NSSA external type 1, N2 – OSPF NSSA external type 2
E1 – OSPF external type 1, E2 – OSPF external type 2
i – IS-IS, su – IS-IS summary, L1 – IS-IS level-1, L2 – IS-IS level-2
ia – IS-IS inter area, * – candidate default, U – per-user static route
o – ODR, P – periodic downloaded static route, H – NHRP, l – LISP
a – application route
+ – replicated route, % – next hop override, p – overrides from PfR
Gateway of last resort is 30.1.1.2 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 30.1.1.2
30.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 30.1.1.0/24 is directly connected, GigabitEthernet0/1
L 30.1.1.1/32 is directly connected, GigabitEthernet0/1
172.16.0.0/16 is variably subnetted, 4 subnets, 2 masks
C 172.16.10.0/24 is directly connected, Tunnel0
L 172.16.10.2/32 is directly connected, Tunnel0
H 172.16.10.3/32 is directly connected, 00:00:02, Tunnel0
H 172.16.10.4/32 is directly connected, 00:00:31, Tunnel0
192.168.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.1.0/24 is directly connected, GigabitEthernet0/0
L 192.168.1.1/32 is directly connected, GigabitEthernet0/0
D % 192.168.2.0/24 [90/28160256] via 172.16.10.3, 02:48:52, Tunnel0
D % 192.168.3.0/24 [90/28160256] via 172.16.10.4, 02:48:52, Tunnel0
Verify HQ Routing
HQ#sh ip route
Codes: L – local, C – connected, S – static, R – RIP, M – mobile, B – BGP
D – EIGRP, EX – EIGRP external, O – OSPF, IA – OSPF inter area
N1 – OSPF NSSA external type 1, N2 – OSPF NSSA external type 2
E1 – OSPF external type 1, E2 – OSPF external type 2
i – IS-IS, su – IS-IS summary, L1 – IS-IS level-1, L2 – IS-IS level-2
ia – IS-IS inter area, * – candidate default, U – per-user static route
o – ODR, P – periodic downloaded static route, H – NHRP, l – LISP
a – application route
+ – replicated route, % – next hop override, p – overrides from PfR
Gateway of last resort is 20.1.1.2 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 20.1.1.2
20.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
C 20.1.1.0/24 is directly connected, GigabitEthernet0/0
L 20.1.1.1/32 is directly connected, GigabitEthernet0/0
172.16.0.0/16 is variably subnetted, 2 subnets, 2 masks
C 172.16.10.0/24 is directly connected, Tunnel0
L 172.16.10.1/32 is directly connected, Tunnel0
D 192.168.1.0/24 [90/26880256] via 172.16.10.2, 02:52:53, Tunnel0
D 192.168.2.0/24 [90/26880256] via 172.16.10.3, 02:52:53, Tunnel0
D 192.168.3.0/24 [90/26880256] via 172.16.10.4, 02:52:53, Tunnel0
Examine IP NHRP on Branch A & HQ Routers
Branch-A#sh ip nhrp brief
****************************************************************************
NOTE: Link-Local, No-socket and Incomplete entries are not displayed
****************************************************************************
Legend: Type –> S – Static, D – Dynamic
Flags –> u – unique, r – registered, e – temporary, c – claimed
a – authoritative, t – route
============================================================================
Intf NextHop Address NBMA Address
Target Network T/Flag
——– ——————————————- —— —————-
Tu0 172.16.10.1 20.1.1.1
172.16.10.1/32 S/
Tu0 172.16.10.3 40.1.1.1
172.16.10.3/32 D/t
192.168.2.0/24 D/t
Tu0 172.16.10.4 50.1.1.1
172.16.10.4/32 D/t
192.168.3.0/24 D/t
Branch-A#
HQ#sh ip nhrp brief
****************************************************************************
NOTE: Link-Local, No-socket and Incomplete entries are not displayed
****************************************************************************
Legend: Type –> S – Static, D – Dynamic
Flags –> u – unique, r – registered, e – temporary, c – claimed
a – authoritative, t – route
============================================================================
Intf NextHop Address NBMA Address
Target Network T/Flag
——– ——————————————- —— —————-
Tu0 172.16.10.2 30.1.1.1
172.16.10.2/32 D/ur
Tu0 172.16.10.3 40.1.1.1
172.16.10.3/32 D/ur
Tu0 172.16.10.4 50.1.1.1
172.16.10.4/32 D/ur
HQ#
Verify Tunnel Interfaces on Branch A and HQ Routers
Branch-A#sh int tun0
Tunnel0 is up, line protocol is up
Hardware is Tunnel
Internet address is 172.16.10.2/24
MTU 17912 bytes, BW 100 Kbit/sec, DLY 50000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation TUNNEL, loopback not set
Keepalive not set
Tunnel linestate evaluation up
Tunnel source 30.1.1.1 (GigabitEthernet0/1)
Tunnel Subblocks:
src-track:
Tunnel0 source tracking subblock associated with GigabitEthernet0/1
Set of tunnels with source GigabitEthernet0/1, 1 member (includes iterators), on interface
Tunnel protocol/transport multi-GRE/IP
Key 0x7B, sequencing disabled
Checksumming of packets disabled
Tunnel TTL 255, Fast tunneling enabled
Tunnel transport MTU 1472 bytes
Tunnel transmit bandwidth 8000 (kbps)
Tunnel receive bandwidth 8000 (kbps)
Tunnel protection via IPSec (profile “JAN-2022”)
Last input 00:00:01, output never, output hang never
Last clearing of “show interface” counters 00:21:53
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 6
Queueing strategy: fifo
Output queue: 0/0 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
308 packets input, 27694 bytes, 0 no buffer
Received 0 broadcasts (0 IP multicasts)
0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
314 packets output, 29020 bytes, 0 underruns
0 output errors, 0 collisions, 0 interface resets
0 unknown protocol drops
0 output buffer failures, 0 output buffers swapped out
Branch-A#
HQ#sh int tun0
Tunnel0 is up, line protocol is up
Hardware is Tunnel
Internet address is 172.16.10.1/24
MTU 17912 bytes, BW 100 Kbit/sec, DLY 50000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation TUNNEL, loopback not set
Keepalive not set
Tunnel linestate evaluation up
Tunnel source 20.1.1.1 (GigabitEthernet0/0)
Tunnel Subblocks:
src-track:
Tunnel0 source tracking subblock associated with GigabitEthernet0/0
Set of tunnels with source GigabitEthernet0/0, 1 member (includes iterators), on interface
Tunnel protocol/transport multi-GRE/IP
Key 0x7B, sequencing disabled
Checksumming of packets disabled
Tunnel TTL 255, Fast tunneling enabled
Tunnel transport MTU 1472 bytes
Tunnel transmit bandwidth 8000 (kbps)
Tunnel receive bandwidth 8000 (kbps)
Tunnel protection via IPSec (profile “JAN-2022”)
Last input 00:00:01, output never, output hang never
Last clearing of “show interface” counters 00:36:16
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 2
Queueing strategy: fifo
Output queue: 0/0 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
1441 packets input, 127644 bytes, 0 no buffer
Received 0 broadcasts (0 IP multicasts)
0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
1446 packets output, 129382 bytes, 0 underruns
0 output errors, 0 collisions, 0 interface resets
0 unknown protocol drops
0 output buffer failures, 0 output buffers swapped out

Sorry, the comment form is closed at this time.