Red Hat Enterprise Linux 9 (RHEL 9) is the latest iteration of the solid Linux OS that powers thousands of Linux servers and workstations at a gazillion companies and organizations worldwide.
So how to quickly verify if the version of Red Hat Enterprise Linux OS you’re running is the latest release, i.e., RHEL 9 aka plow?
There are several ways to confirm if your server has the latest version of the Red Hat OS, i.e., RHEL 9.
Most of the methods do not require sudo (elevated) permission and can be run by all users.
Verify RHEL OS: Many Options
Let’s consider at least 14 ways to verify if your Red Hat workstation or server is running Red Hat Enterprise Linux 9 (RHEL 9).
By the way, all the options below should work well with previous versions of Red Hat OS like RHEL 7 or RHEL 8 as well as CentOS, Rocky Linux and AlmaLinux.
Option 1: Old is Gold
There is one crisp and neat CLI command that’s been providing the answer to the version of Red Hat OS on your server for over 20 years.
That command is cat /etc/redhat-release and it’s been available on RHEL 5, 6, 7, 8 and now on RHEL 9.
$ cat /etc/redhat-release
Red Hat Enterprise Linux release 9.0 (Plow)
Option 2: Via Subscription Manager
The subscription-manager option requires you to have registered your system with Red Hat and also needs administrator privileges.
So what is the Red Hat Subscription Manager?
According to the Red Hat 9 OS man pages, subscription-manager “is a client program that registers a system with a subscription management service such as the Customer Portal Subscription Management service or on-premise Subscription Asset.”
Besides the version of Red Hat OS, the output of sudo subscription-manager facts gives you a ton of other information including CPU, kernel, bios, motherboard and memory.
Since the output is long, I’ve truncated it so you won’t be able to see most of the other information.
$ sudo subscription-manager facts
cpu.core(s)_per_socket: 4
cpu.cpu(s): 8
cpu.cpu_socket(s): 1
cpu.thread(s)_per_core: 2
cpu.topology_source: kernel /sys cpu sibling lists
distribution.id: Plow
distribution.name: Red Hat Enterprise Linux
distribution.version: 9.0
…..[Output Truncated]
Option 3: hostnamectl
hostctl is an elegant CLI command that outputs more than just the Red Hat OS version your system is running.
This command also provides information on the system hardware, kernel, CPU architecture, and Machine and Boot IDs.
Take a look below:
[jack@localhost ~]$ hostnamectl
Static hostname: n/a
Transient hostname: localhost
Icon name: computer-desktop
Chassis: desktop 🖥
Machine ID: 34cbcd014bc4485799485d4322d9d700
Boot ID: aff0229c0ce940c5882014ce732cf194
Operating System: Red Hat Enterprise Linux 9.0 (Plow)
CPE OS Name: cpe:/o:redhat:enterprise_linux:9::baseos
Kernel: Linux 5.14.0-70.22.1.el9_0.x86_64
Architecture: x86-64
Hardware Vendor: Dell Inc.
Hardware Model: OptiPlex 9020
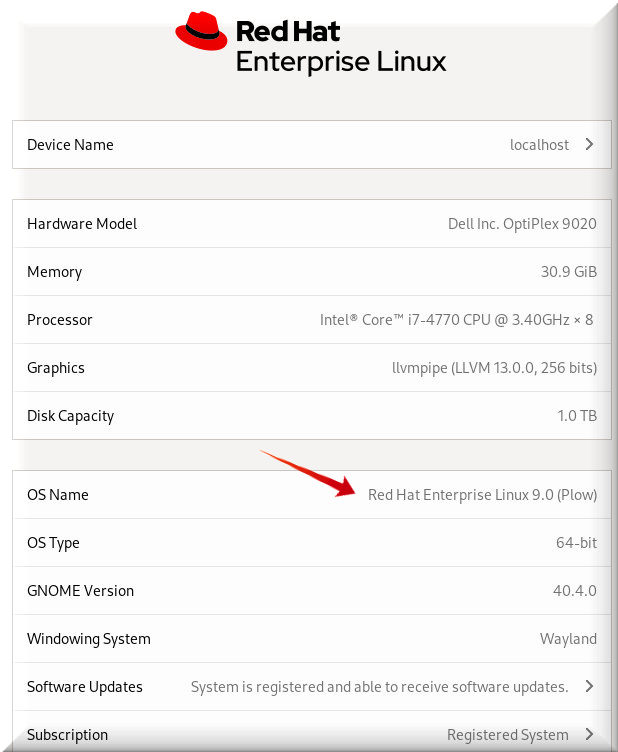
Option 4: Via Gnome Control Center
Our fourth option, gnome-control-center, is actually a combination of CLI and GUI.
You start with the CLI and the output comes in the form of a GUI.
$ gnome-control-center
Option 5: RPM Commands
Let’s now consider a couple of rpm methods to verify the Red Hat release on your server or workstation.
The first method is running a rpm –query:
$ rpm --query redhat-release redhat-release-9.0-2.17.el9.x86_64
Option 6: Another RPM Method
Here’s another rpm way to confirm your RHEL OS version.
This rpm method provides a super-brief answer.
$ rpm -E %{rhel}
9
Option 7: Yet Another cat command
It seems like there’s no end to what you can do with cat, right?
$ cat /etc/os-release
NAME=”Red Hat Enterprise Linux”
VERSION=”9.0 (Plow)“
ID=”rhel”
ID_LIKE=”fedora”
VERSION_ID=”9.0“
PLATFORM_ID=”platform:el9″
PRETTY_NAME=”Red Hat Enterprise Linux 9.0 (Plow)”
ANSI_COLOR=”0;31″
LOGO=”fedora-logo-icon”
CPE_NAME=”cpe:/o:redhat:enterprise_linux:9::baseos”
HOME_URL=”https://www.redhat.com/”
DOCUMENTATION_URL=”https://access.redhat.com/documentation/red_hat_enterprise_linux/9/”
BUG_REPORT_URL=”https://bugzilla.redhat.com/”
Option 8: More the Merrier
The below More command gets to the point quickly.
$ more /etc/redhat-release
Red Hat Enterprise Linux release 9.0 (Plow)
Option 9: Quick One with system-release
$ cat /etc/system-release
Red Hat Enterprise Linux release 9.0 (Plow)
Option 10: cat Offers More
Depending on the cat command, you can get more or less information when you try to verify your version of Red Hat Enterprise Linux.
The below command offers you Red Hat OS version plus provides URL links to Red Hat bug reports and documentation, all right from the terminal.
$ cat /etc/*release
NAME=”Red Hat Enterprise Linux”
VERSION=”9.0 (Plow)“
ID=”rhel”
ID_LIKE=”fedora”
VERSION_ID=”9.0“
PLATFORM_ID=”platform:el9″
PRETTY_NAME=”Red Hat Enterprise Linux 9.0 (Plow)”
ANSI_COLOR=”0;31″
LOGO=”fedora-logo-icon”
CPE_NAME=”cpe:/o:redhat:enterprise_linux:9::baseos”
HOME_URL=”https://www.redhat.com/”
DOCUMENTATION_URL=”https://access.redhat.com/documentation/red_hat_enterprise_linux/9/”
BUG_REPORT_URL=”https://bugzilla.redhat.com/”
REDHAT_BUGZILLA_PRODUCT=”Red Hat Enterprise Linux 9“
REDHAT_BUGZILLA_PRODUCT_VERSION=9.0
REDHAT_SUPPORT_PRODUCT=”Red Hat Enterprise Linux”
REDHAT_SUPPORT_PRODUCT_VERSION=”9.0“
Red Hat Enterprise Linux release 9.0 (Plow)
Red Hat Enterprise Linux release 9.0 (Plow
Option 11: uname it
When you want the RHEL version PLUS the running kernel, go with uname -r
$ uname -r
5.14.0-70.22.1.el9_0.x86_64
Option 12: Another uname CLI
With uname -a, you get the OS version plus today’s date, Kernel and the CPU architecture on your system.
$ uname -a
Linux localhost.localdomain 5.14.0-70.22.1.el9_0.x86_64 #1 SMP PREEMPT Tue Aug 2 10:02:12 EDT 2022 x86_64 x86_64 x86_64 GNU/Linux
Option 13: More cat Stuff
Looks like we’re not going to run out of cat options to verify the Red Hat OS version.
$ cat /etc/system-release-cpe
cpe:/o:redhat:enterprise_linux:9::baseos
Option 14: ls, the Final Method
$ sudo ls /boot/loader/entries | grep el
34cbcd014bc4485799485d4322d9d700-5.14.0-70.13.1.el9_0.x86_64.conf
34cbcd014bc4485799485d4322d9d700-5.14.0-70.22.1.el9_0.x86_64.conf
If you’re a developer you can get access to a free version of Red Hat Enterprise Linux.
Otherwise you’ll have to fork out an annual fee.
Compared to other Linux distros like Ubuntu, familiarity with RHEL OS gives you a better chance of landing a job at a big company or MSP.