In this lab, we’ll configure authentication when running EIGRP in named mode.
While classic mode EIGRP offers only MD5 authentication, named mode EIGRP offers both MD5 and HMAC-SHA-256 authentication.
HMAC-SHA-256 authentication is, of course, the more secure version.
By the way, we can configure authentication between two routers with one running in EIGRP classic mode and the other in EIGRP named mode.
But both would have to use the MD5 authentication mode because EIGRP classic mode does not support HMAC-SHA-256.
Why EIGRP Authentication?
Authentication is essentially a security mechanism to prevent undesirable consequences in the network.
EIGRP router authentication ensures that unauthorized or rogue routers do not become neighbors with other corporate routers.
Unauthorized routers can result in invalid routes and in the worst case scenario lead to data loss or denial of service.
What Our Configuration Looks Like
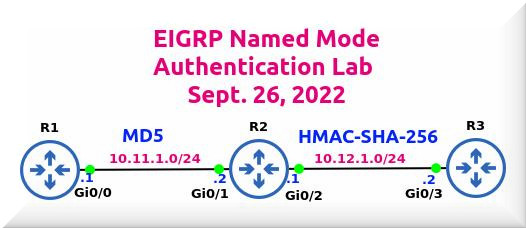
In our setup, we have three routers: R1, R2 and R3.
All of the routers are running EIGRP in named mode.
Between routers R1 and R2, we’ll be configuring MD5 authentication using a key chain.
Key chain does not need to be same on both routers but the Key ID and Key String must be same for both R1 and R2 routers.
Subsequently, we’ll go in for HMAC-SHA-256 authentication between R2 and R3.
HMAC-SHA-256 authentication can be done both without and with a key chain.
Most HMAC-SHA-256 authentication configurations that I have come across do not include a key chain.
Apparently, the key chain feature is not necessary if you’re going with HMAC-SHA-256 authentication.
Between R2 and R3, we’ll first do HMAC-SHA-256 authentication without a key chain and follow it up by adding a key chain to the configuration.
Following the two modes of authentication, we’ll run a bunch of Verify commands to ensure our goals are met.
Configure EIGRP Named Mode Authentication
We’ve configured the IP addresses on the three routers.
IP addresses have already been configured and you can check them by looking at the topology (see at top of this post).
Once again, all three routers are running EIGRP in named mode.
====================
Configure MD5 Authentication between R1 and R2
R1 Configuration
conf t
key chain ROMEO
key 1
key-string Cisco@123
exit
!
router eigrp TESTING
address-family ipv4 unicast autonomous-system 123
network 10.11.1.1 0.0.0.0
!
af-interface gig0/0
authentication mode md5
authentication key-chain ROMEO
!
exit-af-interface
exit-address-family
R2 Configuration
conf t
key chain ROMEO
key 1
key-string Cisco@123
exit
!
router eigrp NESTING
address-family ipv4 autonomous-system 123
network 10.11.1.2 0.0.0.0
network 10.12.1.1 0.0.0.0
!
af-interface gig0/1
authentication mode md5
authentication key-chain ROMEO
exit
! Configuring HMAC-SHA-256 Authentication between R2 and R3
af-interface gig0/2
authentication mode hmac-sha-256 7 Password@1
exit-af-interface
exit-address-family
exit
!
R3 Configuration
conf t
router eigrp PESTING
address-family ipv4 autonomous-system 123
network 10.12.1.2 0.0.0.0
! HMAC-SHA-256 Authentication between R3 and R2
af-interface gig0/3
authentication mode hmac-sha-256 7 Password@1
exit-af-interface
exit-address-family
exit
As you can see above, we’ve not configured a key chain for HMAC-SHA-256 authentication between R2 and R3.
Verify EIGRP Authentication
Having completed the configurations, let’s run a bunch of verify commands.
Verify MD5 Authentication between R1 and R2
R1#sh ip eigrp int detail gig0/0
EIGRP-IPv4 VR(TESTING) Address-Family Interfaces for AS(123)
Xmit Queue PeerQ Mean Pacing Time Multicast Pending
Interface Peers Un/Reliable Un/Reliable SRTT Un/Reliable Flow Timer Routes
Gi0/0 1 0/0 0/0 1594 0/0 7972 0
Hello-interval is 5, Hold-time is 15
Split-horizon is enabled
Next xmit serial
Packetized sent/expedited: 2/0
Hello’s sent/expedited: 92/2
Un/reliable mcasts: 0/2 Un/reliable ucasts: 2/2
Mcast exceptions: 0 CR packets: 0 ACKs suppressed: 0
Retransmissions sent: 1 Out-of-sequence rcvd: 0
Topology-ids on interface – 0
Authentication mode is md5, key-chain is “ROMEO”
Topologies advertised on this interface: base
Topologies not advertised on this interface:
Verify HMAC-SHA-256 Authentication between R2 and R3
R2#sh ip eigrp int detail gig0/2
EIGRP-IPv4 VR(NESTING) Address-Family Interfaces for AS(123)
Xmit Queue PeerQ Mean Pacing Time Multicast Pending
Interface Peers Un/Reliable Un/Reliable SRTT Un/Reliable Flow Timer Routes
Gi0/2 1 0/0 0/0 0 0/0 50 0
Hello-interval is 5, Hold-time is 15
Split-horizon is enabled
Next xmit serial
Packetized sent/expedited: 1/0
Hello’s sent/expedited: 103/2
Un/reliable mcasts: 0/1 Un/reliable ucasts: 3/3
Mcast exceptions: 0 CR packets: 0 ACKs suppressed: 0
Retransmissions sent: 2 Out-of-sequence rcvd: 0
Topology-ids on interface – 0
Authentication mode is HMAC-SHA-256, key-chain is not set
Topologies advertised on this interface: base
Topologies not advertised on this interface:
Check Key Chain on R1
R1#show key chain
Key-chain ROMEO:
key 1 — text “Cisco@123”
accept lifetime (always valid) – (always valid) [valid now]
send lifetime (always valid) – (always valid) [valid now]
Check Key Chain on R2
R2#show key chain
Key-chain ROMEO:
key 1 — text “Cisco@123”
accept lifetime (always valid) – (always valid) [valid now]
send lifetime (always valid) – (always valid) [valid now]
Adding Key Chain on R2 and R3 (HMAC-SHA-256 mode)
R2 Configuration
conf t
key chain JULIET-CHAIN
key 2
key-string Bisco@123
exit
!
router eigrp NESTING
address-family ipv4 autonomous-system 123
af-interface gig0/2
authentication key-chain JULIET-CHAIN
exit
R3 Configuration
conf t
key chain JULIET-CHAIN
key 2
key-string Bisco@123
exit
!
router eigrp PESTING
address-family ipv4 autonomous-system 123
af-interface gig0/3
authentication key-chain JULIET-CHAIN
exit
=================
Verify R2 with HMAC-SHA-256 AND Key Chain
R2#show ip eigrp int detail gig0/2
EIGRP-IPv4 VR(NESTING) Address-Family Interfaces for AS(123)
Xmit Queue PeerQ Mean Pacing Time Multicast Pending
Interface Peers Un/Reliable Un/Reliable SRTT Un/Reliable Flow Timer Routes
Gi0/2 1 0/0 0/0 10 0/0 50 0
Hello-interval is 5, Hold-time is 15
Split-horizon is enabled
Next xmit serial
Packetized sent/expedited: 2/0
Hello’s sent/expedited: 1518/3
Un/reliable mcasts: 0/2 Un/reliable ucasts: 5/4Mcast exceptions: 0 CR packets: 0 ACKs suppressed: 0
Retransmissions sent: 2 Out-of-sequence rcvd: 1
Topology-ids on interface – 0
Authentication mode is HMAC-SHA-256, key-chain is “JULIET-CHAIN”
Topologies advertised on this interface: base
Topologies not advertised on this interface:
Verify Authentication on R3 AFTER Adding Key Chain
R3#show key chain
Key-chain JULIET-CHAIN:
key 2 — text “Bisco@123”
accept lifetime (always valid) – (always valid) [valid now]
send lifetime (always valid) – (always valid) [valid now]

Sorry, the comment form is closed at this time.