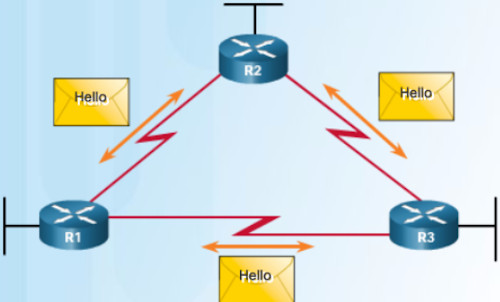
In this third post in our EIGRP series, let’s consider the various packet types used and their purpose. Altogether, we encounter five packet types in EIGRP that are used to establish adjacencies and share routing information. The packet types include: Hello, Acknowledgment, Update, Query and Reply. Some of the EIGRP Read More