In this lab, we’ll do a basic configuration of EIGRP and then run a bunch of verify commands.
We’ll finish off with a ping test to verify end-to-end connectivity between the PCs.
This time the lab is being done on Packet Tracer instead of GNS3. Packet Tracer is easier to set up compared to GNS3 and available as a free download from Cisco.
Another plus with Packet Tracer is that it also runs on different operating systems including Windows, Mac and Linux.
This EIGRP lab is part of Cisco Netacad CCNA curriculum.
The various interfaces on Routers have already been configured and we’ll verify them with the show ip interface brief command.
Passive Interfaces
We’ll also configure passive-interfaces on the three LAN segments attached to R1, R2 and R3.
The point of configuring passive-interfaces is to prevent the LAN interfaces from advertising EIGRP updates.
As part of our EIGRP configuration, we’ll disable auto-summarization and also make the LAN interfaces passive.
Verify Interfaces on Routers
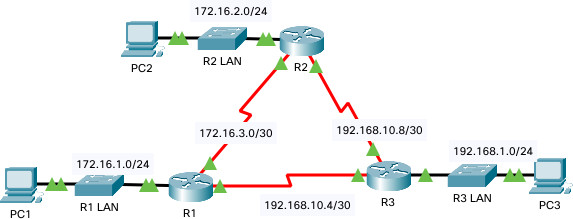
Let’s first take a quick look at the IP addressing on the three routers:
R1#show ip interface brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0/0 172.16.1.1 YES manual up up
GigabitEthernet0/1 unassigned YES unset administratively down down
Serial0/0/0 172.16.3.1 YES manual up up
Serial0/0/1 192.168.10.5 YES manual up up
Vlan1 unassigned YES unset administratively down down
R2#show ip interface brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0/0 172.16.2.1 YES manual up up
GigabitEthernet0/1 unassigned YES unset administratively down down
Serial0/0/0 172.16.3.2 YES manual up up
Serial0/0/1 192.168.10.9 YES manual up up
Serial0/1/0 unassigned YES unset down down
Serial0/1/1 unassigned YES unset administratively down down
Vlan1
R3#show ip interface brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0/0 192.168.1.1 YES manual up up
GigabitEthernet0/1 unassigned YES unset administratively down down
Serial0/0/0 192.168.10.6 YES manual up up
Serial0/0/1 192.168.10.10 YES manual up up
Vlan1 unassigned YES unset administratively down down
The IP addressing looks good on the three routers.
Configure EIGRP Protocol
Now that we’ve verified the interfaces, let’s start configuring EIGRP on the three routers (R1, R2 and R3).
As you can see below, the EIGRP configuration process is simple.
R1(config)# router eigrp 1
network 172.16.1.0 0.0.0.255
network 172.16.3.0 0.0.0.3
network 192.168.10.4 0.0.0.3
no auto-summary
passive-interface g0/0
end
R2(config)# router eigrp 1
network 172.16.2.0 0.0.0.255
network 172.16.3.0 0.0.0.255
network 192.168.10.8 0.0.0.3
no auto-summary
passive-interface g0/0
end
R3(config)# router eigrp 1
network 192.168.10.4 0.0.0.3
network 192.168.10.8 0.0.0.3
network 192.168.1.0 0.0.0.255
no auto-summary
passive-interface g0/0
end
Verify EIGRP Commands
There are a whole bunch of verify commands when it comes to EIGRP.
We’ll run the key ones below.
Let’s start by looking at the Routing Table on R1:
R1#sh ip route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP
i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area
* - candidate default, U - per-user static route, o - ODR
P - periodic downloaded static route
Gateway of last resort is not set
172.16.0.0/16 is variably subnetted, 5 subnets, 3 masks
C 172.16.1.0/24 is directly connected, GigabitEthernet0/0
L 172.16.1.1/32 is directly connected, GigabitEthernet0/0
D 172.16.2.0/24 [90/2170112] via 172.16.3.2, 00:08:06, Serial0/0/0
C 172.16.3.0/30 is directly connected, Serial0/0/0
L 172.16.3.1/32 is directly connected, Serial0/0/0
D 192.168.1.0/24 [90/2170112] via 192.168.10.6, 00:07:38, Serial0/0/1
192.168.10.0/24 is variably subnetted, 3 subnets, 2 masks
C 192.168.10.4/30 is directly connected, Serial0/0/1
L 192.168.10.5/32 is directly connected, Serial0/0/1
D 192.168.10.8/30 [90/2681856] via 172.16.3.2, 00:08:06, Serial0/0/0
[90/2681856] via 192.168.10.6, 00:07:38, Serial0/0/1
The D in the Routing Table indicates the destination network is reachable via EIGRP.
The Administrative Distance (90) and Metric are also shown in the Routing Table. To reach the 172.16.2.0 network, the metric is 2170112.
When you append eigrp to show ip route, you’ll see just the EIGRP routes (see below).
R1#sh ip route eigrp
172.16.0.0/16 is variably subnetted, 5 subnets, 3 masks
D 172.16.2.0/24 [90/2170112] via 172.16.3.2, 00:11:03, Serial0/0/0
D 192.168.1.0/24 [90/2170112] via 192.168.10.6, 00:10:35, Serial0/0/1
192.168.10.0/24 is variably subnetted, 3 subnets, 2 masks
D 192.168.10.8/30 [90/2681856] via 172.16.3.2, 00:11:03, Serial0/0/0
[90/2681856] via 192.168.10.6, 00:10:35, Serial0/0/1</pre
Verifying EIGRP Neighbors on R1:
R1#sh ip eigrp neighbors
IP-EIGRP neighbors for process 1
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 172.16.3.2 Se0/0/0 12 00:12:47 40 1000 0 7
1 192.168.10.6 Se0/0/1 12 00:12:19 40 1000 0 10
Not all routes in the Topology Table get installed into the EIGRP routing table.
Only the “Best Routes” in the EIGRP Topology Table make it to the Routing Table.
Here’s the topology table for R1:
R1#show ip eigrp topology
IP-EIGRP Topology Table for AS 1/ID(192.168.10.5)
Codes: P - Passive, A - Active, U - Update, Q - Query, R - Reply,
r - Reply status
P 172.16.1.0/24, 1 successors, FD is 2816
via Connected, GigabitEthernet0/0
P 172.16.2.0/24, 1 successors, FD is 2170112
via 172.16.3.2 (2170112/2816), Serial0/0/0
P 172.16.3.0/30, 1 successors, FD is 2169856
via Connected, Serial0/0/0
P 192.168.1.0/24, 1 successors, FD is 2170112
via 192.168.10.6 (2170112/2816), Serial0/0/1
P 192.168.10.4/30, 1 successors, FD is 2169856
via Connected, Serial0/0/1
P 192.168.10.8/30, 2 successors, FD is 2681856
via 172.16.3.2 (2681856/2169856), Serial0/0/0
via 192.168.10.6 (2681856/2169856), Serial0/0/1
One of my favorite EIGRP verify commands is show ip protocols.
This command spits out a wealth of information (see below).
R1#sh ip protocols
Routing Protocol is "eigrp 1 "
Outgoing update filter list for all interfaces is not set
Incoming update filter list for all interfaces is not set
Default networks flagged in outgoing updates
Default networks accepted from incoming updates
Redistributing: eigrp 1
EIGRP-IPv4 Protocol for AS(1)
Metric weight K1=1, K2=0, K3=1, K4=0, K5=0
NSF-aware route hold timer is 240
Router-ID: 172.16.1.1
Topology : 0 (base)
Active Timer: 3 min
Distance: internal 90 external 170
Maximum path: 4
Maximum hopcount 100
Maximum metric variance 1
Automatic Summarization: disabled
Automatic address summarization:
Maximum path: 4
Routing for Networks:
172.16.1.0/24
172.16.3.0/30
192.168.10.4/30
Passive Interface(s):
GigabitEthernet0/0
Routing Information Sources:
Gateway Distance Last Update
172.16.3.2 90 743883
192.168.10.6 90 771366
Distance: internal 90 external 170
If you want to check out the interfaces on R1 enabled for EIGRP, there’s a simple command for that.
R1#sh ip eigrp interfaces
IP-EIGRP interfaces for process 1
Xmit Queue Mean Pacing Time Multicast Pending
Interface Peers Un/Reliable SRTT Un/Reliable Flow Timer Routes
Se0/0/0 1 0/0 1236 0/10 0 0
Se0/0/1 1 0/0 1236 0/10 0 0
Ping Test
Let’s do a Ping test on PC1 and see if it can reach PC2 and PC3.
This test will also serve as an end-to-end connectivity check.
PC1 to PC2
Packet Tracer PC Command Line 1.0
C:\>ping 172.16.2.10
Pinging 172.16.2.10 with 32 bytes of data:
Reply from 172.16.2.10: bytes=32 time=1ms TTL=126
Reply from 172.16.2.10: bytes=32 time=1ms TTL=126
Reply from 172.16.2.10: bytes=32 time=1ms TTL=126
Reply from 172.16.2.10: bytes=32 time=1ms TTL=126
Ping statistics for 172.16.2.10:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 1ms, Maximum = 1ms, Average = 1ms
PC1 to PC3
C:\>ping 192.168.1.10
Pinging 192.168.1.10 with 32 bytes of data:
Reply from 192.168.1.10: bytes=32 time=15ms TTL=126
Reply from 192.168.1.10: bytes=32 time=4ms TTL=126
Reply from 192.168.1.10: bytes=32 time=17ms TTL=126
Reply from 192.168.1.10: bytes=32 time=1ms TTL=126
Ping statistics for 192.168.1.10:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 1ms, Maximum = 17ms, Average = 9ms
The two pings from PC1 made it to their destination.
All in all, this lab worked fine and is a good stepping stone to master EIGRP.