In this third post in our EIGRP series, let’s consider the various packet types used and their purpose.
Altogether, we encounter five packet types in EIGRP that are used to establish adjacencies and share routing information.
The packet types include: Hello, Acknowledgment, Update, Query and Reply.
Some of the EIGRP packet types are reliable and require an acknowledgment while others are unreliable and do not need an acknowledgment.
The OPCode field in the EIGRP packet header identifies the packet type:
OPCode 1: Update packet
OPCode 3: Query packet
OPCode 4: Reply packet
OPCode 5: Hello and ACK packets
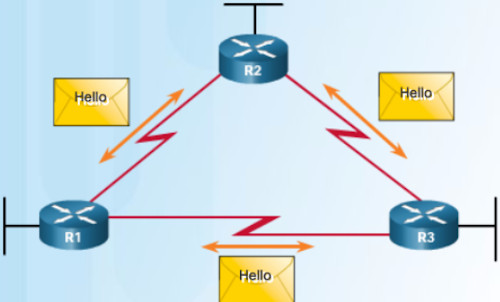
EIGRP Packet Types:
It’s time to consider each of the EIGRP packet types and their purpose.
* Hello:
# Discover and form adacencies with Neighbors (Other EIGRP routers in the NW)
# Hello packets are sent unreliably and do NOT require acknowledgements
# Continued receipt of Hellos maintains Neighbor Table
# Hello packets are sent via multicast
* Acknowledgment:
# Acknowledgements packets are “dataless” Hello packets with just a sequence number
# They indicate receipt of any EIGRP packet during a “reliable” (Reliable Transport Protocol) exchange
# Will acknowledge receipt of Update, Query and Reply packets
* Update:
# Transmit Routability and Reachability information with other EIGRP Neighbors
# Carry prefix and metric information
# Sent to initially exchange topology information or topology change
# Later Updates sent ONLY when necessary, such as when a new destination prefix becomes reachable or the cost of an already reachable destination prefix changes
# So updates are non-periodic, i.e., not sent at scheduled intervals
# EIGRP updates contain only needed routing information and are unicast to routers that require it
# Update packets can also be multicast (like when a link cost changes)
# Sent reliably and require acknowledgments
* Query:
# Query packets are sent when destinations go into Active state
# Used to get specific information from one or more Neighbors; Sent to search for another path during convergence
# Query packets are multicast to all peers on all interfaces except for the interface to the previous Successor
# Sent reliably and require acknowledgements
* Reply:
# Reply packets are unicast to the originator of the query
# Sent reliably and require acknowledgements
Reliable Packets:
Reliable packets require explicit acknowledgement from destination.
They are sequenced and retransmitted up to 16 times if not acknowledged.
Reliable packets are:
• Updates
• Queries
• Replies
• SIA-Queries
• SIA-Replies
Unreliable packets do not require acknowledgement from destination:
# Hello and ACK
How to Verify EIGRP Packets
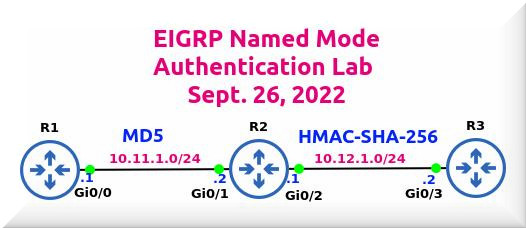
A few days back, we did a basic EIGRP configuration.
As part of that basic EIGRP lab, we ran a bunch of commands including one that let us view the various EIGRP packets on a Router.
Take a look below at various EIGRP Packets on the three Routers R1, R2 and R3:
R1#sh ip eigrp traffic IP-EIGRP Traffic Statistics for process 1 Hellos sent/received: 1211/1170 Updates sent/received: 8/6 Queries sent/received: 0/0 Replies sent/received: 0/0 Acks sent/received: 5/8 Input queue high water mark 1, 0 drops SIA-Queries sent/received: 0/0 SIA-Replies sent/received: 0/0
R2#sh ip eigrp traffic IP-EIGRP Traffic Statistics for process 1 Hellos sent/received: 1167/1162 Updates sent/received: 6/10 Queries sent/received: 0/0 Replies sent/received: 0/0 Acks sent/received: 10/6 Input queue high water mark 1, 0 drops SIA-Queries sent/received: 0/0 SIA-Replies sent/received: 0/0
R3#sh ip eigrp traffic IP-EIGRP Traffic Statistics for process 1 Hellos sent/received: 1140/1137 Updates sent/received: 7/5 Queries sent/received: 0/0 Replies sent/received: 0/0 Acks sent/received: 5/6 Input queue high water mark 1, 0 drops SIA-Queries sent/received: 0/0 SIA-Replies sent/received: 0/0